Smart offices are revolutionizing the way we work, offering unprecedented opportunities to enhance productivity, efficiency, and employee experience. However, this digital transformation also introduces significant challenges, particularly in the realm of data security and privacy. This article explores the multifaceted landscape of data in AI-powered smart offices, examining the benefits, risks, and essential strategies for creating a secure and human-centered workspace.
The Rise of the Intelligent Workspace
Smart offices leverage a variety of technologies, including Artificial Intelligence (AI), Internet of Things (IoT) devices, and data analytics, to create intelligent and responsive environments. These technologies generate vast amounts of data, offering valuable insights that can be used to optimize office operations and improve the overall work experience.
Data-Driven Benefits
- Enhanced Efficiency: AI algorithms can analyze data from sensors and building management systems to optimize energy consumption, adjust lighting and temperature, and automate routine tasks. This leads to significant cost savings and a reduced environmental footprint.
- Improved Productivity: Smart office technologies can streamline workflows, facilitate collaboration, and provide employees with personalized support. For example, AI-powered meeting room management systems can automatically schedule meetings, optimize room utilization, and provide real-time information on availability.
- Enhanced Security: AI-powered security systems can monitor access points, detect anomalies, and respond to potential threats in real-time. These systems can also be used to improve cybersecurity by identifying and mitigating potential vulnerabilities.
- Personalized Experiences: Smart offices can collect data on employee preferences and behaviors to create personalized work experiences. This includes adjusting lighting and temperature to individual preferences, providing personalized recommendations for meeting spaces, and offering customized training and development opportunities.
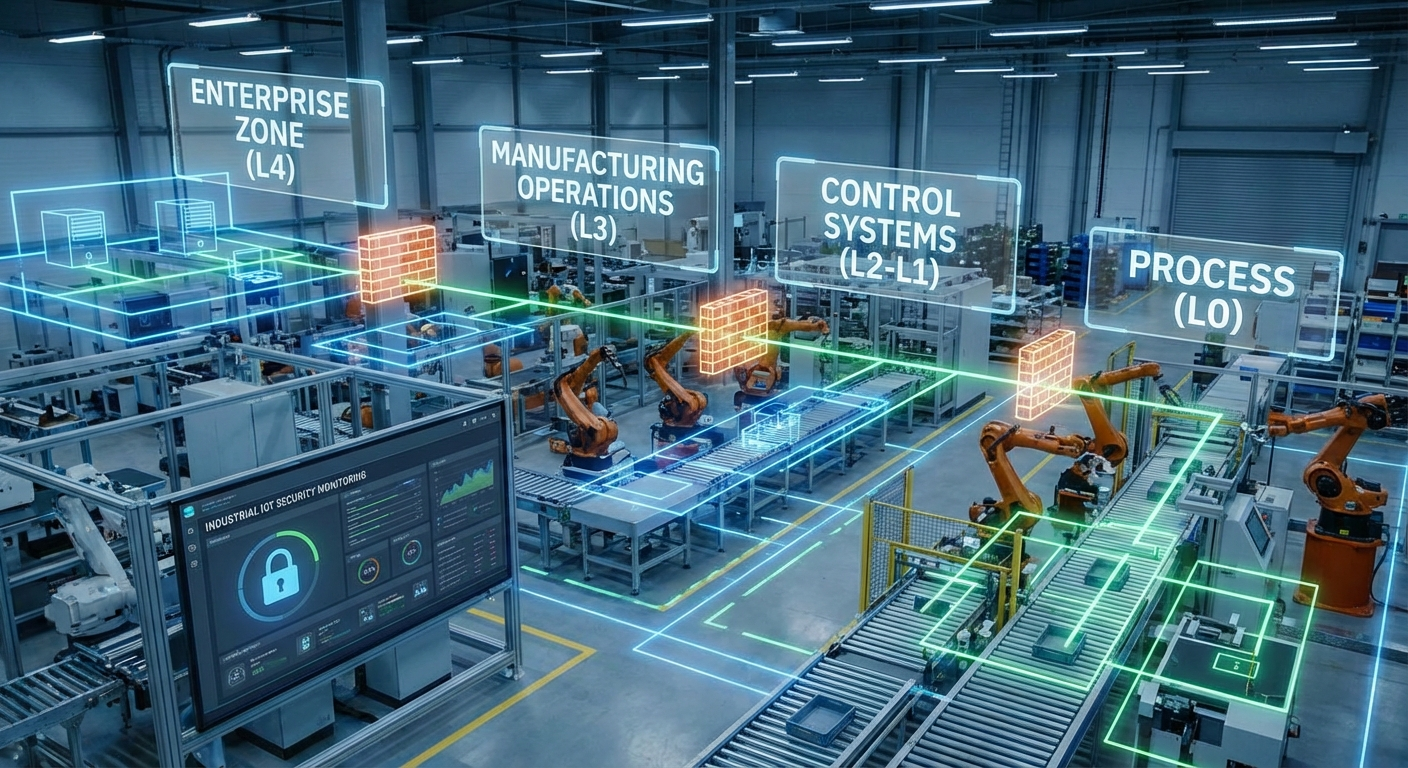
The data ecosystem within a smart office is complex and diverse, encompassing a wide range of sources and types:
- Building Management Systems (BMS): BMS data includes information on energy consumption, HVAC (heating, ventilation, and air conditioning) performance, lighting, and other building systems.
- IoT Sensors: IoT devices, such as occupancy sensors, smart lighting, and environmental monitors, generate real-time data on space utilization, environmental conditions, and employee movements.
- Access Control Systems: Access control systems collect data on employee entries and exits, providing insights into building security and space utilization.
- Network and Device Data: Data from office networks and employee devices can provide insights into application usage, network performance, and potential security threats.
- Employee Activity Data: Data from collaboration platforms, communication tools, and productivity applications can offer insights into employee workflows, communication patterns, and productivity levels.
- Surveys and Feedback: Employee surveys and feedback mechanisms can provide valuable qualitative data on employee satisfaction, preferences, and needs.
Navigating the Data Security and Privacy Risks
While the benefits of data-driven smart offices are undeniable, it is crucial to acknowledge and address the inherent security and privacy risks.
Cybersecurity Threats
Smart offices, like every server on the internet, are prone to be hacked. The increased interconnectedness of devices and systems creates a larger attack surface for cybercriminals. A single vulnerability in an IoT device or network can be exploited to gain access to sensitive data or disrupt critical office operations.
- Data Breaches: Cyberattacks can result in the theft of sensitive employee data, including personal information, financial records, and health information.
- Ransomware Attacks: Ransomware attacks can encrypt critical office systems and data, demanding a ransom payment for their release.
- Denial-of-Service (DoS) Attacks: DoS attacks can flood office networks with traffic, disrupting critical services and preventing employees from accessing essential resources.
- Insider Threats: Malicious or negligent employees can intentionally or unintentionally compromise data security.
Privacy Concerns
The collection and use of employee data in smart offices raise significant privacy concerns.
- Surveillance: The use of sensors and monitoring systems can create a feeling of constant surveillance, leading to employee stress and reduced morale.
- Data Misuse: Employee data can be used for purposes beyond their original intent, such as making discriminatory employment decisions or sharing data with third parties without consent.
- Lack of Transparency: Employees may not be fully aware of the types of data being collected, how it is being used, and who has access to it.
- Data Retention: Data may be retained for longer than necessary, increasing the risk of breaches and misuse.
Addressing the Challenges
To mitigate these risks and ensure the responsible use of data in smart offices, organizations must adopt a comprehensive and proactive approach to security and privacy.
Building a Secure Smart Office Ecosystem
Creating a secure smart office requires a holistic strategy that encompasses technology, policies, and people.
1. Establish a Robust Security Foundation
- Cybersecurity Framework: Develop and implement a comprehensive cybersecurity framework based on industry best practices and standards. This framework should include policies, procedures, and controls for data protection, access control, incident response, and vulnerability management.
- Network Segmentation: Segment the office network to isolate critical systems and data from less secure areas. This can help prevent attackers from gaining access to sensitive resources even if they compromise a single device or system.
- Endpoint Security: Implement endpoint security solutions on all employee devices, including laptops, smartphones, and tablets. These solutions should include antivirus software, firewalls, and intrusion detection systems.
- IoT Security: Secure IoT devices by changing default passwords, disabling unnecessary services, and implementing network segmentation. Regularly update the firmware on IoT devices to patch security vulnerabilities.
- Data Encryption: Encrypt sensitive data both in transit and at rest. Use strong encryption algorithms and manage encryption keys securely.
- Multi-Factor Authentication (MFA): Implement MFA for all critical systems and applications. MFA adds an extra layer of security by requiring users to provide multiple forms of authentication, such as a password and a one-time code from a mobile app.
- Regular Security Audits: Conduct regular security audits to identify vulnerabilities and assess the effectiveness of security controls. Engage external security experts to perform penetration testing and vulnerability assessments.
- Incident Response Plan: Develop and maintain an incident response plan to address security breaches and other incidents. The plan should outline procedures for identifying, containing, eradicating, and recovering from security incidents.
Securing Smart Offices in the Era of Smart Cities: Strategies for a Connected WorldIntroduction
The emergence of smart cities has brought about a revolution in urban living, and parallelly, the concept of smart offices is transforming the business world. This article explores the relationship between smart offices and smart cities, focusing on the importance of securing these interconnected environments. The Synergy of Networks,![]() Secure IoT OfficeSecure IoT Office
Secure IoT OfficeSecure IoT Office
2. Prioritize Data Privacy
- Data Minimization: Collect only the data that is necessary for specific and legitimate purposes. Avoid collecting excessive or irrelevant data.
- Transparency and Consent: Be transparent with employees about the types of data being collected, how it is being used, and who has access to it. Obtain informed consent from employees before collecting and using their data.
- Data Governance Policy: Develop a comprehensive data governance policy that outlines the principles, rules, and responsibilities for managing data within the organization. The policy should address data quality, data security, data privacy, and data retention.
- Privacy-Enhancing Technologies (PETs): Explore the use of PETs, such as data anonymization, differential privacy, and homomorphic encryption, to protect employee privacy while still enabling data analysis.
- Data Retention Policy: Establish a data retention policy that specifies how long data will be retained and when it will be securely deleted. Avoid retaining data for longer than necessary.
- Data Subject Rights: Respect employee data subject rights, including the right to access, correct, and delete their personal data. Provide employees with easy-to-use mechanisms for exercising their data subject rights.
- Privacy Impact Assessments (PIAs): Conduct PIAs before deploying new smart office technologies or data analytics initiatives. PIAs help identify and mitigate potential privacy risks.
3. Foster a Culture of Security and Privacy
- Employee Training: Provide regular security and privacy training to all employees. The training should cover topics such as data security best practices, phishing awareness, password security, and data privacy regulations.
- Security Awareness Programs: Implement security awareness programs to promote a culture of security within the organization. These programs can include security newsletters, posters, and simulated phishing attacks.
- Incident Reporting: Encourage employees to report security incidents and privacy breaches promptly. Establish clear channels for reporting incidents and provide assurance that reports will be investigated and addressed.
- Open Communication: Foster open communication between management and employees about security and privacy concerns. Create a safe space for employees to voice their concerns and provide feedback.
4. Embrace a People-Centered Approach
- Employee Involvement: Involve employees in the design and implementation of smart office technologies. Solicit their feedback and address their concerns.
- Ergonomics and Well-being: Prioritize employee ergonomics and well-being when designing smart office spaces. Ensure that workstations are adjustable, lighting is appropriate, and noise levels are minimized.
- Accessibility: Ensure that smart office technologies are accessible to all employees, including those with disabilities. Follow accessibility guidelines and standards when designing user interfaces and developing applications.
- Flexibility and Choice: Provide employees with flexibility and choice in how they use smart office technologies. Allow them to customize their work environment and choose the tools that best suit their needs.
- Continuous Improvement: Continuously monitor and evaluate the effectiveness of smart office technologies and security and privacy controls. Make adjustments as needed to improve performance, security, and employee satisfaction.
The Future of Secure Smart Offices
The future of smart offices will be shaped by several key trends:
- AI-Powered Security: AI will play an increasingly important role in security, enabling real-time threat detection, automated incident response, and predictive security analytics.
- Privacy-Enhancing Technologies: PETs will become more widely adopted as organizations seek to balance data innovation with data privacy.
- Zero-Trust Security: Zero-trust security models, which assume that no user or device can be trusted by default, will become more prevalent.
- Edge Computing: Edge computing, which processes data closer to the source, will reduce latency, improve security, and enable new smart office applications.
- Human-Centered Design: Human-centered design principles will be at the forefront of smart office development, ensuring that technologies are designed to meet the needs and preferences of employees.
Conclusion
AI-powered smart offices offer tremendous potential to transform the way we work, but they also introduce significant data security and privacy risks. By adopting a comprehensive and proactive approach to security and privacy, organizations can mitigate these risks and create secure, human-centered workspaces that enhance productivity, efficiency, and employee well-being. As smart office technologies continue to evolve, it is essential to remain vigilant, adapt to emerging threats, and prioritize the responsible use of data. By embracing these principles, organizations can unlock the full potential of smart offices while safeguarding the security and privacy of their employees.