Welcome to the new era of work – the smart office. Our walls are embedded with technology, our systems are interconnected, and our operations are increasingly reliant on a network of intelligent devices. From automated climate control and smart lighting to collaborative digital workspaces and advanced security systems, the smart office promises enhanced efficiency, productivity, and a more dynamic work environment. However, this digital transformation also introduces a critical consideration: cybersecurity.
As a smart office, I am more than just a physical space; I am a cyber-physical system (CPS). My interconnected devices, powered by the Internet of Things (IoT), create a vast network that, while offering numerous benefits, also presents an expanded attack surface for malicious actors. Just as critical infrastructure in smart cities faces heightened cyberattack risks, so too does the integrated technology within a smart office.
Smart City Cybersecurity Assessment | CyberSafe.CityComprehensive security assessment for smart city technologies. Evaluate risks, get recommendations, and protect your urban infrastructure.![]() CyberSafe.City
CyberSafe.City Consider the landscape of my operations:
Consider the landscape of my operations:
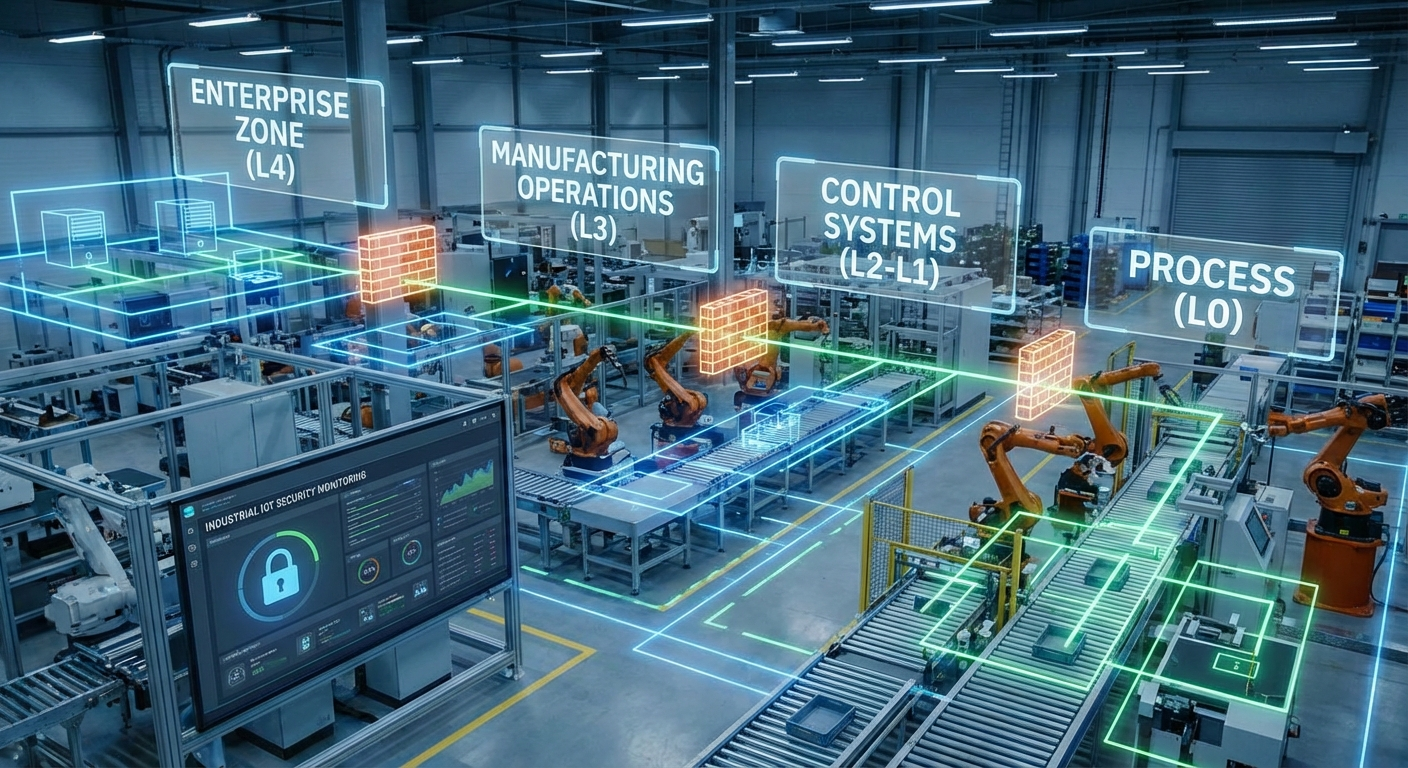
- Building Management Systems (BMS): Controlling HVAC, lighting, and energy consumption, these systems are now often IP-enabled, creating potential entry points for cyber threats.
- Networked Printers and Copiers: These devices can store sensitive information and, if not properly secured, can be exploited to gain access to the internal network.
- Smart Security Systems: While designed to protect the physical space with smart locks, surveillance cameras, and access control, these systems themselves can be vulnerable to cyberattacks, potentially allowing unauthorized entry or disabling security measures.
- Collaborative Digital Workspaces: Platforms for video conferencing, file sharing, and project management are essential for modern work but require robust security to protect sensitive business data.
- Employee Devices: Laptops, smartphones, and tablets, often connected to the office network, can be vulnerable endpoints if not managed and secured properly.
A Smart Home’s Perspective: Balancing Convenience and Cyber Concerns in the Interconnected CityHello. I am not a person, but I am a home. A smart home, to be precise. My walls have seen the evolution of urban living, and now, I am deeply integrated into the fabric of a smart city. My purpose is to enhance the lives of my residents, to![]() Secure IoT HouseSecure IoT House
Secure IoT HouseSecure IoT House
Smart Office Security Scorecard | IoT Device Risk AssessmentEvaluate your smart office security posture with our comprehensive IoT device risk assessment tool.Secure IoT Office
 Key Cybersecurity Best Practices for a Secure Smart Office:
Key Cybersecurity Best Practices for a Secure Smart Office:
Drawing on the cybersecurity best practices highlighted in the sources, here’s how a smart office must approach security:
- Comprehensive Risk Assessment and Vulnerability Management: The first crucial step is to recognize vulnerabilities across all interconnected systems. A comprehensive risk assessment will identify potential risks and security gaps, allowing for the development of targeted defenses. Understanding the vulnerabilities in IoT devices and critical infrastructure interdependencies is paramount.
- Development and Implementation of Robust Cybersecurity Policies and Procedures: Written cybersecurity policies and procedures for all employees are vital. These should address acceptable use of devices and the network, strong password management, access control (including the principle of least privilege), and guidelines for personal mobile devices used for work.
- Secure Design and Implementation: Security must be built into the smart office infrastructure from the outset (“security-by-design”). This includes secure hardware and software, strong encryption for data at rest and in transit, and secure coding practices.
- Network Segmentation: Dividing the office network into smaller, isolated segments can limit the damage caused by a cyberattack. If one segment is compromised, the attacker’s ability to move laterally across the entire network is significantly reduced.
- Strong Identity and Access Management (IAM): Enforcing IAM best practices, such as multi-factor authentication (MFA), is essential to protect employee identities and control access to sensitive data and systems. This can stop initial attacks before they lead to lateral movement or privilege escalation.
- Incident Response Planning: Preparing for cyberattacks is not optional; it’s a necessity. A comprehensive written incident response plan is crucial for quickly identifying, investigating, responding to, and restoring critical systems and networks after an incident. These plans should include roles and responsibilities for all stakeholders.
- Supply Chain Risk Management: Managing risks associated with our technology vendors is critical. We must use trusted vendors and set security requirements for all software and hardware suppliers, scrutinizing their access to our data.
- Operational Resilience and Business Continuity: Developing contingencies for manual operations of critical functions and training staff accordingly ensures that basic services can continue even if the smart systems are compromised. Regularly exercising incident response and recovery plans, and coordinating with continuity managers, is vital.
- Continuous Monitoring and Threat Detection: Implementing 24x7 monitoring, detection, and response capabilities is crucial. Partnering with third-party security operations providers can provide the necessary expertise and technology to swiftly detect and respond to threats. Anomaly Behavior Analysis (ABA) intrusion detection systems can be applied to protect critical components.
- Employee Cybersecurity Awareness Training: The human element is often the weakest link in the security chain. Regular workforce training on cybersecurity threats, such as phishing emails and social engineering, and best practices is essential to empower employees as a line of defense.
- Data Privacy Considerations: As a smart office, we collect data on building usage, employee activity, and more. Protecting data privacy is paramount. We must be transparent about our data collection practices and implement privacy-focused design principles.
Smart Home Security Scorecard | Risk Assessment ToolComprehensive security assessment tool for premium smart homes. Evaluate your IoT devices, network, and privacy protection with our interactive assessment.![]() Smart Home Security ScorecardSecure IoT House
Smart Home Security ScorecardSecure IoT House The Importance of Collaboration:
The Importance of Collaboration:
Securing a smart office is not a solitary endeavor. Collaboration between our organization, technology providers, and even other businesses is essential for sharing threat intelligence and best practices. Public-private partnerships, as highlighted in the context of smart cities, can enhance our overall security posture.
The Evolving Threat Landscape:
The cyber threat landscape is constantly evolving. We must remain vigilant and adapt our security measures to address emerging threats, including ransomware attacks, which can have significant financial and operational impacts. Understanding the methodologies of threat actors, including state-sponsored groups, cybercriminals, and insider threats, is crucial for developing effective defenses.
Smart office devices that are interconnected within smart cities.
- Smart Meters (Electricity, Gas, Water): These are key components of a smart city’s energy and utility infrastructure. While located within an office building, they directly interface with the city-wide smart grid for real-time data on consumption and management. Compromising a smart meter in an office could potentially lead to inaccurate billing, service disruption for the office, or even be a point of entry to the office’s internal network or the wider smart city infrastructure.. The “Advanced Metering Infrastructure” is specifically listed as a cyber-physical technology in the electricity subsector of smart cities.
- Building Management Systems (BMS): These systems control critical functions within a smart office, such as HVAC, lighting, and energy consumption. In a smart city context, these BMS are often networked and integrated for optimized energy management across the city. These IP-enabled systems can be attractive targets, and their compromise could lead to operational disruptions within the office, allow for unauthorized access, or potentially be leveraged to attack other interconnected city systems.
- Smart Security Systems: This includes smart locks, access control systems, and surveillance cameras. While securing the office itself, these systems often connect to broader city-wide security networks for monitoring and response. For example, law enforcement surveillance systems are often internet-connected. Vulnerabilities in these smart office security devices could grant unauthorized physical access to the office or allow attackers to gain insights into building activities, potentially impacting the security of the wider smart city if these systems are interconnected for city-wide safety initiatives.
- Networked Printers and Copiers: These office staples, when connected to the network (as is the norm in smart offices), become part of the interconnected ecosystem. While not always considered core “smart city” devices, they can be exploited to gain access to the office network, which is part of the larger city network. These devices can store sensitive information and act as potential entry points for lateral movement within the interconnected infrastructure.
- Smart Lighting Systems: Integrated within a smart office and often managed by the BMS, these systems can also be part of a city’s smart energy initiatives. Their connectivity makes them potential targets, and while the direct impact might seem limited to the office’s lighting control, compromised systems could be used as a stepping stone for further network intrusion.
- Intelligent Transportation Systems (ITS) Interfaces: While not located inside the office, systems that directly interface with a smart city’s ITS can impact the office. For example, smart parking systems used by employees, real-time traffic information displays within the office, or systems for managing company fleets rely on the interconnectedness of the smart city’s transportation infrastructure. Security vulnerabilities in these interfaces or the underlying ITS could disrupt office operations related to transportation and logistics.
A Smart Home’s Perspective: Balancing Convenience and Cyber Concerns in the Interconnected CityHello. I am not a person, but I am a home. A smart home, to be precise. My walls have seen the evolution of urban living, and now, I am deeply integrated into the fabric of a smart city. My purpose is to enhance the lives of my residents, to![]() Secure IoT HouseSecure IoT House
Secure IoT HouseSecure IoT House
In conclusion, the smart office offers tremendous potential, but its realization hinges on a strong foundation of cybersecurity. By proactively addressing vulnerabilities, implementing robust security measures, fostering a culture of security awareness, and embracing collaboration, we can navigate the cyber landscape and ensure a secure and productive future for the smart office. Our commitment to security is not just about protecting our assets; it’s about maintaining the trust and integrity of our operations in this interconnected world.